Your monthly cybersecurity update
by Florence
Posted on 29-09-2020 02:39 AM
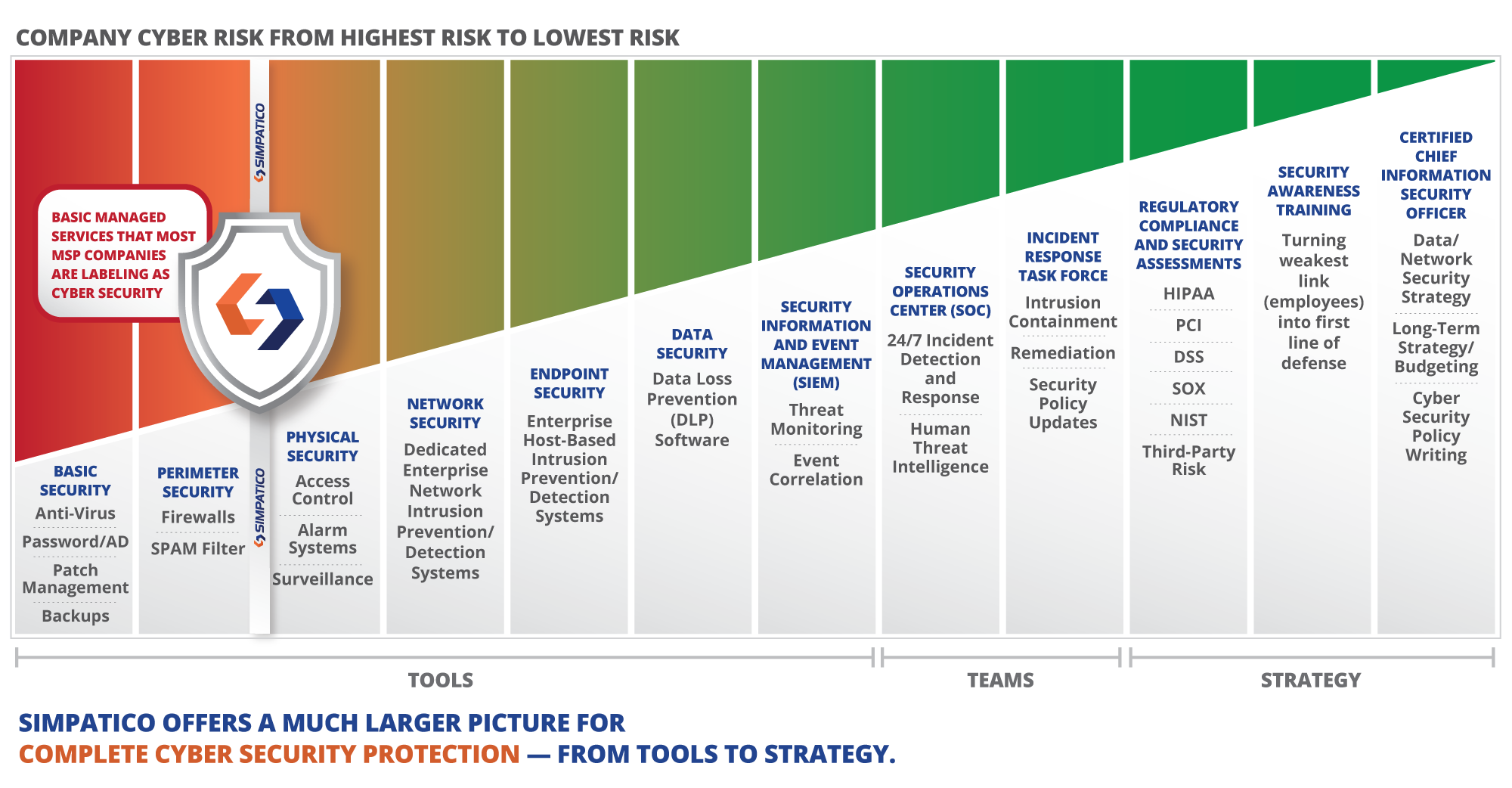
A cyber security index (or threat level indicator) can be found on a variety of publicly available sources.

WE MITIGATE CYBER SECURITY RISKS THAT
Can i balance information protection and accessibility?
what does a ‘good’ cyber security strategy look like in my sector?
can i prioritize cyber risks based on my company’s strategy?
how do i determine the right level of investment?
where should i put my investments?
how can i prevent or mitigate the disruption of a cyber event?.

Success lies in mitigating breaches before they happen, and self-learning to prevent future incidents: all while ensuring business continuity across the enterprise. Fujitsu intelligence-led security gives you the tools and technologies you need to robustly manage your cyber security. Enjoy complete visibility of events to identify threats early-on, and routine scanning of systems to detect vulnerabilities before they are exploited. Meanwhile, external intelligence provides an overview of current and emerging risks as well as your overall cyber security novelty gifts gifts for cybersecurity professionals gifts for cyber security geeks posture.
Alternative faq phrasings: what is a cybersecurity? | what is cyber security? definition: cybersecurity (a. K. A. Cyber security, computer network security) refers to the specialization of computer network security that consists of technologies, policies, and procedures that protect networked computer systems from unauthorized use or harm. Broadly speaking, cybersecurity topics can be subdivided into two complementary areas: cyber attacks , which are essentially offensive and emphasize network penetration techniques; and cyber defenses , which are essentially protective and emphasize counter-measures intended to eliminate or mitigate cyber attacks.
Ampcus cyber enables cloud threat defense providing defense to threats in a cloud system requires new and evolving ai-driven approach. This approach correlates the various security data sets that include network traffic, dicey configurations, user activity and threats that provide an allied view of the risks that are present across the disintegrated cloud environment.
CYBER SECURITY PROGRAM DEVELOPMENT
Comments: 0
the federal cyber security market research provides a brief analysis comprising both primary and secondary research.

Summary: curriculum not available. Available information suggests there is no such program on cyber security.
With a world-class measurement and testing laboratory encompassing a wide range of areas of computer science, mathematics, statistics, and systems engineering, nist’s cybersecurity program supports its overall mission to promote u. S. Innovation and industrial competitiveness by advancing measurement science, standards, and related technology through research and development in ways that enhance economic security and improve our quality of life.
“entrepreneur of the year 2016†award by entrepreneurs council of india. “vinutna ratna awardâ€, by akkineni foundation of usa, for his achievements in the field of cyber security. Winner of bug bounty programs of uber and shopify. Speaker and panelist at ficci (federation of india chamber of commerce & industry). National technical committee member at national cyber security novelty gifts gifts for cybersecurity professionals gifts for cyber security geeks and safety standards.
Global cyber security of security hardware market 2020 rnm newly added a research report on the cyber security of security hardware market, which represents a study for the period from 2020 to 2026. The research study provides a near look at the market scenario and dynamics impacting its growth. This report highlights the crucial developments along with other events happening in the market which are marking on the growth and opening doors for future growth in the coming years. Additionally, the report is built on the basis of the macro- and micro-economic factors and historical data that can influence the growth.
CYBER SECURITY RISK ASSESSMENT
Janelle romano recognized for extraordinary work in maryland cybersecurity industry reduce risk of network compromises nsa releases cybersecurity technical report on uefi secure boot customization nsa named agency of the year for combined federal campaign nsa, national cryptologic museum foundation reveal design plans for state-of-the-art cyber center for education and innovation.
No other certification that assesses baseline cybersecurity skills has performance-based questions on the exam. Security+ emphasizes hands-on practical skills, ensuring the security professional is better prepared to problem solve a wider variety of issues. More choose security+ for dod 8570 compliance than any other certification. Security+ focuses on the latest trends and techniques in risk management, risk mitigation, threat management and intrusion detection.
3rd Party Security Assurance
From passive recon to compromise w/ osint & third party apps | tyrone e. Wilson hacker halted 2019: keynote speaker – tyrone e. Wilson “the keyboard doesn’t lieâ€: a conversation with army veteran, hacker, and cybersecurity entrepreneur: tyrone e. Wilson who’s your hacker con – passive recon the academy | a day in the life of a pentester | a conversation with tyrone e. Wilson and jorge orchilles.
Network & IT Security
C | eh v10 - certified ethical hacker training ethical hacking - c | ehp e | csa | ec - council certified security analysis c | swd - certified secure web developer iot penetration testing training network penetration testing - c | npt web application penetration testing - c | wapt reverse engineering and malware analysis co.
With more and more devices connected to the internet, the public safety infrastructure is not as secure or as closed as sometimes believed. Each networked device is a potential entry point for a cyber attacker, and managing security for every device that can potentially connect to the network is overwhelming. Criminals and state-sponsored actors across the globe find these vulnerabilities and exploit them, launching cyber-attacks at an ever-increasing pace. They want to disrupt your communications and they intend to impact your emergency response.
Our security specialists will create an impenetrable computer network defense to fend off cyberattacks. Your company’s privacy and security need to be taken seriously if you want to avoid the cruel fate of having hackers hijack your company. One of the best ways to ensure total protection is to implement a comprehensive security scheme that goes beyond running a basic antivirus application on your desktops.
Technology allows individuals and organizations access to more comprehensive and diverse information, but this access requires that electronic information, networks, data repositories, and data transmissions be adequately safeguarded. Rand has developed a large body of research focused on recognizing the potential threats to information security and data integrity, as well as implications for personal and institutional privacy.
Improve efficiency, speed, and performance of test labs with security threats increasing in frequency, the need for effective cyber and security testing is also on the rise. You need to optimize your cyber and security test labs to improve efficiency, speed, and performance. Cyber and security test lab challenges traditional test labs can be exceedingly wasteful due to ongoing infrastructure costs coupled with poor utilization. Test lab professionals are under growing pressure to rapidly configure complex network topologies in order to execute test scenarios without increasing operating expenses caused by labor intensive and error prone methods. Cyber and security testing adds additional stress as a result of demanding time constraints and an increased need for efficient network topology changes.
Today’s ever-evolving threats require a new way of thinking to safeguard the integrity of your operations. We take a revolutionary new approach with a “baked in†versus “bolted on†security solution that can be dropped into your existing network, while leveraging your legacy devices and infrastructure. Our solutions protect critical infrastructure and information across a broad range of industries.
Stellar cyber effectively pieces together complex cyber attacks across the entire it infrastructure esg showcase stellar cyber improves security operations efficacy, efficiency, and productivity download the report stellar cyber leads with built in network traffic analysis, siem and response download the report.
Cyber and IT Solutions
The fusion cyber solutions program provides local school districts with the ability to build the capacity to fully integrate online learning into their schools. Fusion is not a cyber school; rather, it is an online learning initiative that involves a comprehensive shift in the way we envision our public schools. As our world and the growing number of students enrolled in cyber schools have indicated, there is an undeniable need for all schools to embrace online learning as a viable option for students. Our goal is for each district will be able to offer the majority of their curriculum in both an online format and face-to-face, resulting in an education system where students can move seamlessly between classroom and online courses. This gives districts the ability to provide students with the flexibility of online courses without leaving the district. Through the fusion program, all district teachers will gain the required skills necessary to create and teach high-quality, rigorous, and engaging online courses that are aligned to their district’s curriculum. The consortium of schools participating in the fusion program allows for sharing of courses and resources, giving districts the opportunity to develop their online learning initiatives over time. The fusion program can be customized to meet individual district needs to successfully carry them through the 21st century.
Cyber Risk Management Solutions
Protecting industrial control systems and ot networks from a cyber pandemic journey to the cloud with confidence view all sep 15 2020 - sep 24 2020 teissr3 online summit 2020 - online (english) sep 22 2020 - sep 24 2020 microsoft ignite 2020 – virtual event - online (english) sep 23 2020 - sep 24 2020
living in the age of data means embracing the interconnectedness that allows us to communicate and collaborate in an infinite number of ways. Data can mean a wealth of information and insight at our fingertips, but it can also be detrimental in the wrong hands. With progressively more information traveling over the wires and with increasing threats internationally with cyber terrorism, the need to defend and protect an organization’s assets is critically important.
Search
Categories
- Songwriter
- Resident Care
- Retirement
- Runner
- Sailor
- Helmsman
- Grammar Police
- Flight Attendant
- Fisher
- Entertainer
- Editor
- Daily Nutritinionist Facts
- Cyber Security
- Crusader
- Criminology
- Coworker
- Clinical Specialist
- Clinical
- Optometrist
- Logistician
- Magistrate
- Manicurist
- Marines
- Marketer
- Occupation
- Observer
- Officer
- Oncologist
- Painter
- Lifeguard
- Infopreneur
- Nanny
- Cartographer
- Expediter
- ESL Teacher
- Comedian
- Estimator
- Flagger
- Discjokey
- Driving
- Electrologist
- Fumigator
- Erector
- Driller
- Educator
- Dressmaker
- Forensic
- Legislator
- Harvester
- Cooker
- Inspector
- Hacker
- Civil Law
- Employer
- Enologist
- Endocrinologist
- Freelancer
- Enrobing
- Fabricator
- Forecaster
- Clown
- Criminologist
- Collector
- Docent
- Concierge
- Conservator
- Digger
- Dishwasher
- Drafter
- Donor
- Controller
- Communication
- Compounder
- Civil
- Clone
- Doctor
- Cinematographer
- Chiropractor
- Rugger
- Bailbondsman
- Jailer
- Deckhand
- Bellman
- Social Worker
- Babysitter
- Reporter
- Trainer
- Agent
- Embroiderer
- Sociologist
- Pharmacist
- Paramedic
- Insurance
- Teller
- Actuary
- Bailiff
- Coordinator
- Carpenter
- Cleaner
- Academic Dean
- Judge
- Boilermaker
- Clerk
- Apprentice
- Secretary
- Author
- Embalmer
- Hiker
- Cooking
- Deputy Sheriff
- Landscaper
- Photographer
- Pediatrician
- Pilot
- Teacher
- Archivist
- Toolmaker
- Singer
- Racer
- Accounting
- Mentor
- Vice President
- Detective
- Waiter
- Florist
- Broker
- Consultant
- Geographer
- Adjuster
- Auctioneer
- Researcher
- Cardiologist
- Marketing
- Interviewer
- Custodian
- Curator
- Caretaker
- Butcher
- Martial Arts
- Ghostbuster
- Mayor
- Machinist
- Innkeeper
- Mediator
- Conductor
- Demonstrator
- Programmer
- Cabinet Maker
- Planner
- Patient
- Copywriter
- Mechanic
- Surfer
- Employee
- Tour Guide
- Fisherman
- Surveyor
- Manager
- Supervisor
- Appraiser
- Police
- Filmmaker
- Woodworker
- Lecturer
- Inventor
- Liaison Officer
- Laborer
- Translator
- Janitor
- Tailor
- Debater
- Climber
- Politician
- Journalist
- Dietitian
- Firefighter
- Adjudicator
- Producer
- Housekeeper
- Entrepreneur
- Bartender
- Barista
- Hairstylist
- Banker
- Baker
- Electrician
- Therapist
- Astronaut
- Professor
- Architect
- Announcer
- Veterinarian
- Scientist
- Investigator
- Dispatcher
- Creative Writing
- Engineer
- Librarian
- Wanker
- Psychology
- Lieutenant
- Realtor
- Pastor
- Biker
- Nutrition
- Dancer
- Musician
- Gardener
- Farmer
- Counselor
- Boss
- Director
- Dentist
- Lawyer
- Nurse
- Accountant
- Coach
- Advisor
- Beekeeper
- Administrator